Lately I have been using JBoss more and more as my deployment platform of choice. I am currently using the latest JBoss Enterprise Middleware solution (EAP version 5.0.1). This is a commercial version, but you can also use the community edition as well which offers most of the same features.
One of the issue I have encountered recently was how to secure the web based administration consoles?
As a matter of fact, the default installation offers a login and password for the admin console which is typically accessible on http://localhost:8080/admin-console if your web application runs locally, or more generally on http://<host>:<port>/admin-console.
However if you want to protect the JMX console (http://localhost:8080/jmx-console) and the JBoss Web console (http://localhost:8080/web-console) you have to make sure that certain files in your installation are setup correctly.
Generally, the JBoss community and RedHat are quite good at documenting the features of their products, but I was disappointed to find incomplete information in the main page on this subject.
This page explains that "the jmx-console and web-console are standard servlet 2.3 deployments that can
be secured using J2EE role based security. Both also have a skeleton setup to allow one to easily enable security using username/password/role mappings found in the jmx-console.war and web-console.war deployments in the corresponding WEB-INF/classes users.properties and roles.properties files".
To secure the JMX Console using a username/password file -
The author probably assumes that the various locations are obvious to everyone. Let me be more precise and generous in details:
First you will need to know which profile/configuration you are running. JBoss EAP has six configurations based on your needs:
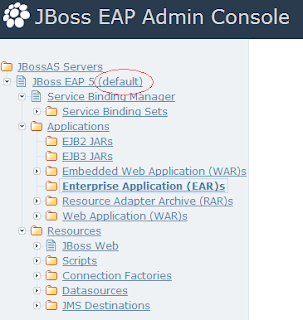
You can check which profile is running by looking at your JBoss EAP Admin Console. The name of the profile/configuration is indicated at the top of the server hierarchy.
By the way, the various applications that you will likely developed (war, ear, rar or jar files) will be deployed under the corresponding folders under the Applications node.
First you might want to change the login and password of the admin console itself before adding those for the JMX and Web consoles?
One important "meta" file is login-config.xml which is located under \jboss-as\server\
This file specify for a specific profile (e.g. default) the security-domain values for the consoles:
In other words, this file can help you locate and map how authentication (login and password in users.properties file) and authorization (access control in roles.properties file) is specified.
Since these consoles are themselves web applications, you will need to look at exploded war files under your profile, under the deploy folder.
Securing the JMX Console:
Securing the Web Console:
One of the issue I have encountered recently was how to secure the web based administration consoles?
As a matter of fact, the default installation offers a login and password for the admin console which is typically accessible on http://localhost:8080/admin-console if your web application runs locally, or more generally on http://<host>:<port>/admin-console.
However if you want to protect the JMX console (http://localhost:8080/jmx-console) and the JBoss Web console (http://localhost:8080/web-console) you have to make sure that certain files in your installation are setup correctly.
Generally, the JBoss community and RedHat are quite good at documenting the features of their products, but I was disappointed to find incomplete information in the main page on this subject.
This page explains that "the jmx-console and web-console are standard servlet 2.3 deployments that can
be secured using J2EE role based security. Both also have a skeleton setup to allow one to easily enable security using username/password/role mappings found in the jmx-console.war and web-console.war deployments in the corresponding WEB-INF/classes users.properties and roles.properties files".
Until this point, it is quite clear. The difficulty starts with a vague description where to find the files in questions :
- Locate the directory. This will normally be in directory..
First you will need to know which profile/configuration you are running. JBoss EAP has six configurations based on your needs:
- all (everything, including clustering support and other enterprise extensions)
- default (for application developers)
- minimal (the strict minimum)
- production (everything but optimized for production environments)
- standard (tested for Java EE compliance)
- web (experimental lightweight configuration)
run.sh -c you most likely use the default profile.
You can check which profile is running by looking at your JBoss EAP Admin Console. The name of the profile/configuration is indicated at the top of the server hierarchy.
By the way, the various applications that you will likely developed (war, ear, rar or jar files) will be deployed under the corresponding folders under the Applications node.
First you might want to change the login and password of the admin console itself before adding those for the JMX and Web consoles?
One important "meta" file is login-config.xml which is located under \jboss-as\server\
This file specify for a specific profile (e.g. default) the security-domain values for the consoles:
<application-policy name = "jmx-console">
<authentication>
<login-module code="org.jboss.security.auth.spi.UsersRolesLoginModule"
flag="required">
<module-option name="usersProperties">props/jmx-console-users.properties</module-option>
<module-option name="rolesProperties">props/jmx-console-roles.properties</module-option>
</login-module>
</authentication>
</application-policy>
<application-policy name = "web-console">
<authentication>
<login-module code="org.jboss.security.auth.spi.UsersRolesLoginModule"
flag="required">
<module-option name="usersProperties">web-console-users.properties</module-option>
<module-option name="rolesProperties">web-console-roles.properties</module-option>
</login-module>
</authentication>
</application-policy>
In other words, this file can help you locate and map how authentication (login and password in users.properties file) and authorization (access control in roles.properties file) is specified.
Since these consoles are themselves web applications, you will need to look at exploded war files under your profile, under the deploy folder.
Securing the JMX Console:
- Locate the folder jmx-console.war under ./server/<config>/deploy
- Open the file ./server/<config>/deploy/mx-console.war/WEB-INF/web.xml
- Verify that the <security-constraint> section is not commented (in this section, you should see specified the roles for authorization (see below)
<security-constraint>
<web-resource-collection>
<web-resource-name>HtmlAdaptor</web-resource-name>
<description>An example security config that only allows users with the
role JBossAdmin to access the HTML JMX console web application
</description>
<url-pattern>/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>JBossAdmin</role-name>
</auth-constraint>
</security-constraint>
- Locate the file: .\server\<config>\conf\props\jmx-console-users.properties (if the file name has not been changed in login-config.xml)
- change admin=admin to your new <new_login>=<new_password>
<login-config>
<auth-method>BASIC</auth-method>
<realm-name>JBoss JMX Console</realm-name>
</login-config>
<security-role>
<role-name>JBossAdmin</role-name>
</security-role>
Securing the Web Console:
- Login credentials are the same as used for the JMX console - in : .\server\<config>\conf\props\jmx-console-users.properties
- change admin=admin to your new <new_login>=<new_password>
For more information and this topic you can also look at Securing the JMX Console and Web Console (HTTP).



